Documentation
Alerts for Microsoft 365 app configuration
Exchange Online Access
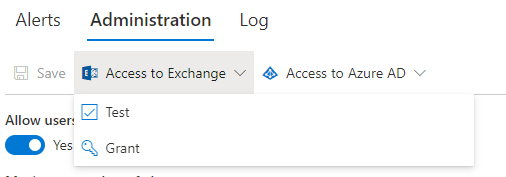
The app can be granted permissions to send emails through your Exchange Online mailboxes. For that, a Global administrator needs to grant the app the permission to send via users' mailboxes. The permissions is granted through a special button on:
- Alerts -> Administration tab.
- Global Settings -> Alerts
The grant is identical, it doesn't matter where it is granted from.
If the permission is not granted, alerts are sent through the built-in outgoing email functionality of SharePoint, which imposes several restrictions on the functionality:
- No external recipients
- No attachments
- No control over From account (always send from no-reply@sharepointonline.com)
The permissions grant page is opened in a pop-up window, please make sure it's allowed to open by your pop-up blocker.
Specifying sender mailbox
By default, alerts can only be sent from the mailbox of the alert creator. If you would like to send from a different account you would need to configure a list of Authorized senders at a site collection (Alerts -> Administration) or tenant level (Global Settings). Tenant-level settings can also override and block site collection level settings.
To specify Authorized senders at a site collection level:
- Open the main page for alert management as a site collection administrator and a Global Administrator of the tenant.
- Switch to Administration tab
- Check "Allow changes to sender".
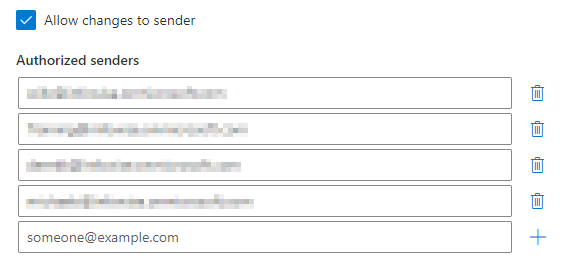
- Specify authorized senders. Each one has to be an existing mailbox in your Exchange Online. Note: distribution list emails are not supported.
- Site collection administrators can, if allowed by the tenant administrator, now enter any valid mailbox email and regular users can only pick from authorized senders specified at site collection or tenant level.
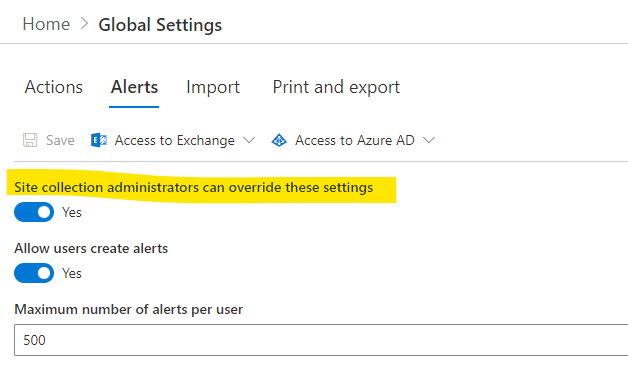
Tenant-level settings are similar, except for being accessed from Global Settings -> Alerts.
Site collection settings override tenant (Global) settings, unless tenant setttings disallow that.
Security Trimming
By default, the app will ensure that every recipient who is a tenant user has at least Read access to the item. If such access cannot be determined, the recipient is removed. Note that by default we cannot check membership of Azure Active Directory groups. To enable that, a global administrator must grant the app the right to query group membership in Azure AD. The permission is granted via a special button under Alerts -> Administration or Global Settings.
You can also disable security trimming at site collection or tenant level.
