Enabling Self-Service Password Change via SharePoint & Ultimate Forms
Changing passwords is one of the most frequent IT support tasks. Users forget their passwords, need to rotate them, or get locked out—leading to help desk tickets and productivity delays. A self-service password change experience (where users can change their domain password from a web portal) improves user satisfaction, reduces support load, and increases security posture.
With Infowise Ultimate Forms and its Manage Active Directory action, you can build such a self-service password change portal inside SharePoint—letting users change passwords from a custom form, without needing to open AD management consoles or scripts.
In this article, we’ll explore how password change works under the hood, how Ultimate Forms supports it, how to configure it, and best practices to make it secure and reliable.
Infowise Ultimate Forms & the Manage Active Directory Action
Ultimate Forms offers a built-in Manage Active Directory action as part of its Actions component. This action supports several operations including:
-
Reset password — changing a user’s password.
-
Update user — including set other user properties.
-
Create, enable, disable, add to/remove from groups, etc.
Specifically for password change, you can configure an action of type Reset password. This can be triggered from a form (e.g. a “Change Password” form), or via a button, conditionally, or as part of a workflow.
In SharePoint (on-prem or hybrid), the action may run under an account with AD privileges or using impersonation, depending on your infrastructure. On Microsoft 365 / Entra ID, you must grant the proper API permissions (Graph API) for managing user passwords.
In summary, Ultimate Forms gives you the ability, within a no-code environment, to hook up a password-change UI to AD or Entra ID, respecting directory protocols and security.
Designing the Self-Service Change Password Interface
Here’s how you would design the password-change experience in SharePoint + Ultimate Forms.
1. Create a Change Password List & Form
-
Create a SharePoint list (e.g. “Password Change Requests”) with columns
New Password andConfirm Password. -
Use the Ultimate Forms Form Designer to create a form with columns for new and confirm.
-
Use validation rule to ensure
New Password = Confirm Password. It will prevent mismatch between the values and block saving otherwise. You can also use pattern-based validation rules to ensure password complexity.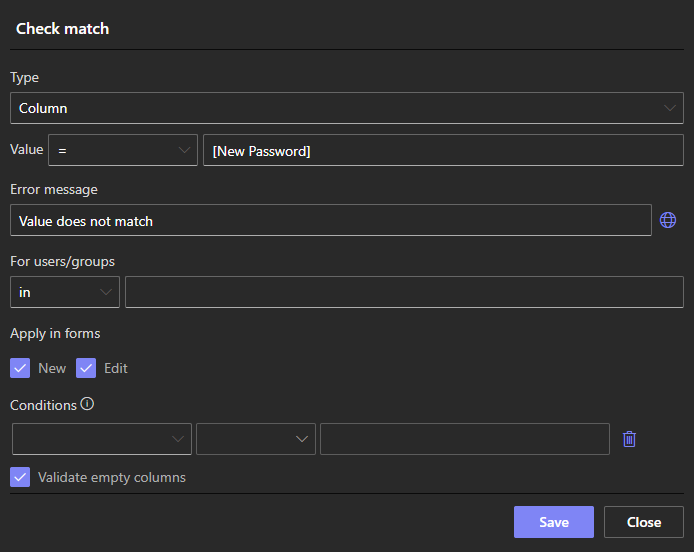
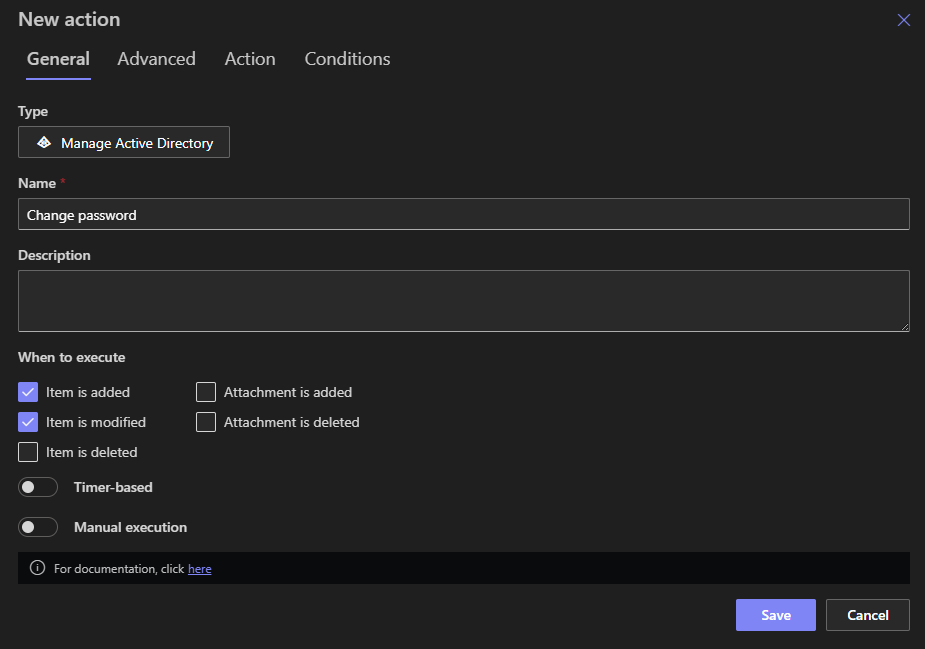
2. Configure an Action: Reset Password
-
In that list’s Actions settings, add an action of type Manage Active Directory → Reset password.
- Map the
User namecolumn to Created By value andNew Passwordcolumn in your action configuration. Using Created By ensures that users can only change their own passwords.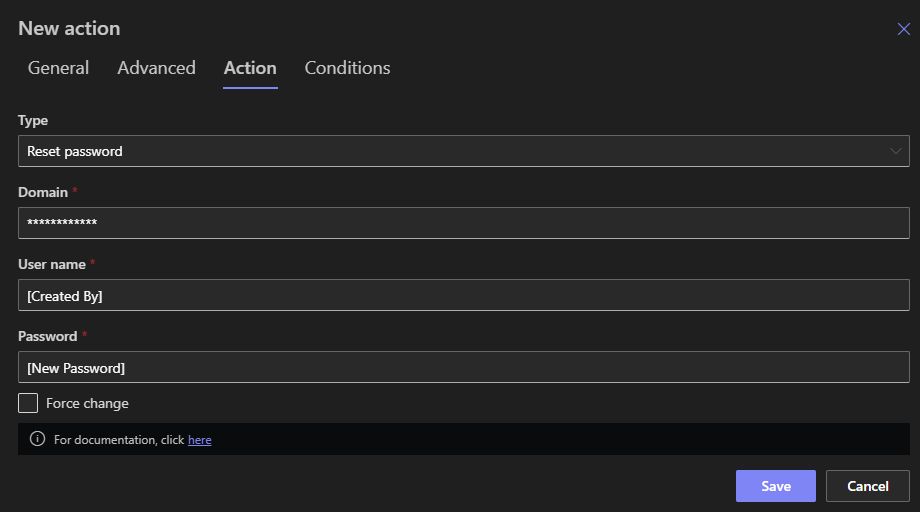
- Use error handling: if AD refuses the change (e.g. password policy violation), catch and return meaningful error.
3. Optional Step: Clear Sensitive Columns
After the password-change action runs, you will user another action to clear or mask the New Password and Confirm Password column values to avoid leaving sensitive data in the list.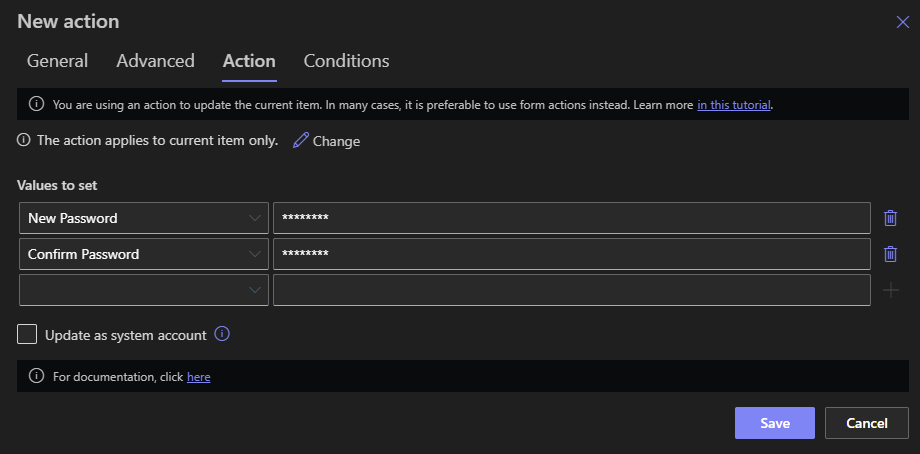
4. Provide Feedback to the User
- Optionally, send an email notification to the user confirming the change (without revealing the password).
5. Permissions & Visibility
-
Only allow users to see and edit their own password-change items. Use list permissions or row-level logic to restrict visibility.
-
Hide/disable admin operations on the form for regular users.
6. Test & Validate
-
Test with different user accounts.
-
Use invalid/new password that breaks policy to confirm proper error messages.
-
Confirm the new password actually works for domain authentication (e.g. user can log in) and replicates.
-
Make sure error paths don’t leak sensitive information.
-
Test in various contexts (on-prem, hybrid, cloud) to ensure the action’s AD connectivity is reliable.
Use Cases & Scenarios
Use Case A: Self-Service Password Change for End Users
End users log into a SharePoint portal where they see a “Change My Password” link. They enter current and new password, hit “Change,” and the action triggers the password change in AD via the configured Manage AD action—all within SharePoint.
Use Case B: Helpdesk-Assisted Reset
A help desk user has elevated permissions. They access a form where they enter a user account and a new password. A password reset action runs with “Reset Password” permissions to change it centrally.
Use Case C: Expiration Flow / Prompt to Change
You might use a scheduled action or form logic to flag accounts approaching expiration. Users click a “Change Password” form before expiration. That form triggers the same AD reset logic.
Best Practices & Security Considerations
-
Always use secure channels (SSL / Encryption)
AD password changes must be transmitted over secure channels. Ensure your SharePoint front-end to AD communication is encrypted (LDAP over SSL, secure Graph API). -
Limit action permissions
Only the service account or application running the Manage AD action should have reset privileges. Don’t expose full AD admin rights to all UI users. -
Validation & policy enforcement
In your form logic, pre-check password complexity rules rather than waiting for AD to reject. That improves usability. -
Audit & logging
Log the fact, time, and user of password change attempts (and failures). Store logs in a secure, tamper-evident location. -
Protect new and confirm password columns
Treat those data columns as sensitive. Use masked input controls, restrict list visibility, avoid storing clear text for longer than necessary. -
Error handling & user messaging
Don’t expose raw AD errors to users. Translate errors to user-friendly messages (e.g. “Password too weak, try longer/complex”), while logging full technical detail for admins. -
Testing & rollback
Try many scenarios — invalid passwords, policy violations, network errors, AD unavailability. Have fallback methods (e.g. contact support) in case the automated path fails. -
Limit reset attempts / guard against abuse
Use throttling or rate limits so malicious users cannot brute force resets. -
Replication delay awareness
In multi-domain environments, allow for time delays or cache invalidation so new password becomes effective across the network. -
Encryption in transit & at rest
Ensure that password values in transit (during action execution) are never stored unencrypted. Intermediate logs or temp data should be protected.
Summary
Allowing users to change their own Active Directory passwords through a SharePoint-based interface helps streamline support, improve user satisfaction, and strengthen security. With Infowise Ultimate Forms’ Manage Active Directory action, you can build this functionality in a no-code environment—creating a password-change form, hooking up AD reset logic, handling errors, and respecting security concerns.
